Common security threats
Browsing the internet connects you with millions of other users and computers around the world. Some of these users choose to exploit this connectivity for malicious purposes such as stealing data or manipulating IT systems.
Here are some examples of security threats, how to avoid them and how to report them.

Malware
Malware is any unwanted software that is installed without the user’s consent. It is used to disrupt computer operations, collect data or otherwise gain unauthorised access to computer systems.
Email: Cybercriminals are notorious for including malicious attachments and links in emails that appear to come from trusted sources.
Websites: Many websites exist which if visited will attempt to infect your computer with malware. When browsing the internet ensure that you visit only trustworthy sites.
Unsecured networks: Connecting to unknown networks can leave your device vulnerable to malware. Public wireless access points are especially insecure.
- Install anti-malware software onto your computer and run periodic full system scans.
- Do not open email attachments from unfamiliar sources.
- Be cautious when browsing the web, do not visit a site which does not look legitimate.
- Be cautious with USB drives. Do not connect unknown USB drives to your computer.
- Popup ads appear even when your browser is not open.
- A security program you didn't install displays warnings.
- Posts that you didn't write appear on your social media pages.
- A program holds your PC for ransom.
- Suddenly you can't use common system tools.
For staff:
- Disconnect your computer from the internet.
- Contact IDS Service Desk.
- Change your passwords from an uninfected computer.
For students:
- Install anti-malware/antivirus software to attempt to remove the malicious software. Ensure that you run a full scan of your system.
- If antivirus not successful disconnect computer from internet.
- Change your passwords from an uninfected computer.
- Restore – Seek malware removal servies.

Phishing
Phishing is attempting to maliciously acquire information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity.
- Contains unusual links
- Asks recipient to provide personal details
- Appears to be from a well-known organisation
- Official looking logos
- Unusual attachments
- Spelling mistakes
- Report the email.
- DO NOT click on any links in the email.
- DO NOT supply any personal information of any kind as a result of the email.
- DO NOT reply to the email or attempt to contact the senders in any way.
- DO NOT open any attachments that arrive with the email.
- DELETE the email from your computer as soon as possible.
- Delete any unsolicited email from an organisation (Flinders or otherwise) that asks you to provide sensitive personal information or account information.
- Never click on a link in an email, always manually type website addresses into your browser/search engine instead.
It is imperative that you act quickly to protect your Flinders University account.
- Report the email.
- Change your password immediately by visiting the Change your FAN password webpage.

Spam
Spamming refers to the use of electronic messaging systems (email) to indiscriminately send unsolicited bulk messages (spam), especially advertising.
At the University, 70-80% of our emails are rejected as spam. Although most of the spam sent to Flinders University email addresses is filtered, some of it may inadvertently slip through.
Spam can easily be identified by:
- The email address. A long string of alphanumeric characters before the @ suggests the email is spam.
- What comes after the @. Emails from respected companies or well-established websites will not have an email address from a provider such as accounts.flinders@gmail.com.
- A sense of urgency. If the email demands action is taken quickly, it is a reasonable indication of spam.
- Links within the message. A legitimate email from a respectable company would ask you to log into your account to make changes, not via an email link.
- Grammatical and spelling errors within the email message.
Spam and phishing emails are closely linked and are often confused however may both have undesirable consequences to University and personal information.
Stay vigilant, do not follow links or open attachments in emails that you do not recognise.
- Report the email.
- Delete it from your inbox, ensuring that you do not open any attachments or follow any links within the email.

Spyware
Spyware gathers information about a person or organisation without their knowledge and may send this information to another entity without consent. Spyware is a form of malware.
The University maintains anti-virus and email filtering technology to minimise the likelihood of spyware infections.
You can further reduce risk of infection when using a University device by:
- Only downloading files from reputable sources and in formats that you recognise.
- Be security conscious, do not open email attachments from unfamiliar sources.
- Be cautious when browsing the web, do not visit a site that does not look legitimate.
- Trust your instincts – if it doesn’t look right, it probably isn’t.
- New toolbars added to your browser without your knowledge.
- Your browser navigation gets redirected.
- Your homepage, mouse pointer or search engine changes unexpectedly.
- Popup ads appear even when no browser is open or the internet is not connected.
- Computer performance has noticeably declined.
For staff:
- Disconnect your computer from the internet.
- Contact IDS Service Desk.
- Change your passwords from an uninfected computer.
For students:
- Install anti-malware/antivirus software to attempt to remove the malicious software. Ensure that you run a full scan of your system.
- If antivirus not successful disconnect computer from internet.
- Change your passwords from an uninfected computer.
- Restore – Seek malware removal servies.
Emails
To help staff identify phishing email attempts, alerts are displayed on incoming emails received from an external source.
Below is an image of the banner you will see alerting you to be cautious.

If you do not trust the source, do not click any links or attachments in the email, but report it, so IDS can investigate further.
- The banner is preventing visibility of the Outlook preview screen because phishing emails will use the preview screen to hook you into an action quickly, without having time to check the message thoroughly.
- You can delete the banner from email replies if you are concerned about how it will be regarded by the recipient.
- We will not be allowing any external email addresses to bypass this banner, nor will we be reintroducing the preview screen for external emails - doing so would introduce greater risk of phishing attacks.
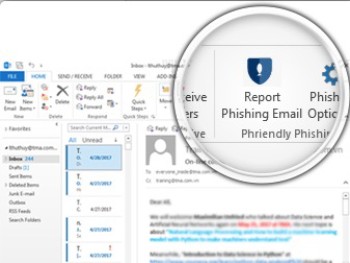
Reporting Suspicious Messages
If you do suspect an email is suspicious or phishing related, report the email by clicking ‘Report Phishing Email’. By reporting the email, it will be automatically deleted and placed into your Deleted Items folder. Note, the first time you use the “Report Phishing Email” button, you may be prompted to log in to Microsoft365 using your Okta credentials. This will only occur the first time you use the button.
Support for digital and IT services
Opening hours: 8am to 6pm, Monday to Friday, excluding public holidays
After hours or when all staff are busy you will be given an option to leave a voicemail message. Voicemails will be accessed as soon as practical during business hours otherwise you may choose to log an IT support request.
![]()
Sturt Rd, Bedford Park
South Australia 5042
CRICOS Provider: 00114A TEQSA Provider ID: PRV12097 TEQSA category: Australian University
This website uses cookies
Flinders University uses cookies to ensure website functionality, personalisation and a variety of purposes as set out in its website privacy statement. This statement explains cookies and their use by Flinders.
If you consent to the use of our cookies then please click the button below:
If you do not consent to the use of all our cookies then please click the button below. Clicking this button will result in all cookies being rejected except for those that are required for essential functionality on our website.





